What is Packet Sniffing (Quick & Simple Guide)

Keep hearing about packet sniffing, and don’t know what it is?
It’s a topic you’ll hear more and more about in the near future, so it’s a good thing you decided to learn about it right now. We’ll do our best to make this topic as simple to understand as possible in this quick guide.
What Is Packet Sniffing?
Packet sniffing is the process of collecting and analyzing all the data packets that pass through a network. For example, someone snooping on your DNS queries is a form of packet sniffing.
This process is performed with the help of packet sniffers (also called packet analyzers).
Is Packet Sniffing Illegal?
It’s hard to say. If you google “packet sniffing laws,” you won’t really find a lot of information. At most, we managed to find this WIRED article from 2010. Unfortunately, it’s not really reliable since it’s pretty old + there’s no clear conclusion.
As far as we can tell, the only correct answer right now is “it depends.” Each country, county, state, and locality handles packet sniffing in different ways. What might be legal in one place can be completely illegal in a different region.
But we’re not going to leave you hanging. Obviously, using packet sniffing with the intention of stealing login credentials or spying on people’s online habits is normally illegal. The same goes for setting up your own WiFi network to logging people’s traffic - especially if you create a “fake” hotspot that imitates legit networks.
The only acceptable use case would be if you were an ethical hacker that wanted to teach people about the dangers of free, unencrypted WiFi. Even then, though, you couldn’t impersonate legitimate networks.
If you’re a network admin at a company, however, things are a bit different. In that case, it’s usually legal for employers to use packet sniffers.
Why?
Because they actually have legitimate use cases:
- Network analysis and troubleshooting.
- Performance analysis and benchmarking.
- Detecting network issues and security loopholes.
- Maintaining network WiFi uptime.
- Making sure employees don’t intentionally or unintentionally put company data at risk.
Packet Sniffing Tools - Hardware and Software
There are actually two types of packet sniffers: hardware and software. Even though software packet sniffers are the most popular ones, we figured we should also tell you about hardware packet analyzers.
1. Hardware Packet Sniffers
These are small tools that are plugged into a network (so a modem or router). Businesses use them a lot because they’re pretty good at logging traffic from specific network segments. That helps prevent packet loss due to filtering or routing issues. Also, a hardware packet sniffer can either store logs or forward them to a collector.
We haven’t really heard about hackers using hardware packet analyzers on public computers. But that doesn’t mean they can’t compromise devices at hotels, Internet cafes, or libraries. They do that with keyloggers, so there’s nothing stopping them from doing it with hardware packet sniffers.
Not to mention they don’t even need to buy expensive tools since they can easily make their own.
2. Software Packet Sniffers
They’re basically programs you download and install on your computer. Then, you use it to collect and analyze all the traffic flowing through the network you’re connected to. Software packet sniffers have two components:
- The network adapter - It’s responsible for connecting the tool to the network.
- The software - Basically an interface that lets people collect, log, and analyze data packets.
Wireshark is really a good example of such a packet analyzer. It’s open-source and free, and surprisingly user-friendly. A cybercriminal would just need to install it on their device, and use it to spy on the right network adapter.
Here’s an example of what someone would see with Wireshark if they were to monitor your DNS queries.
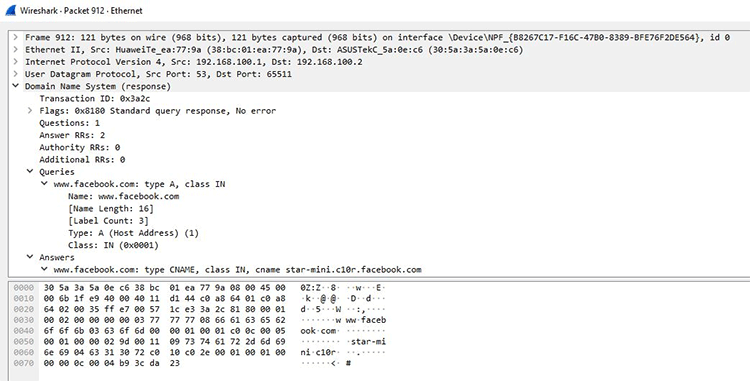
Please note how it’s very easy to see where connection requests are heading (www.facebook.com in this photo). It’s right under Queries.
How Dangerous Is Packet Packet Sniffing?
If it’s done for legitimate reasons (like network troubleshooting at your company), it’s relatively safe. Employers can already spy on everything you do on the work computer, so packet sniffing isn’t something you should be particularly concerned about.
What about WiFi packet sniffing? Like when you use public networks?
That’s a whole different story.
If cybercriminals use packet sniffers to listen in on your traffic, things can get bad really fast. For example, they could intercept your data packets to HTTP sites, and see your login credentials, what you’re typing, and what files you’re downloading or uploading.
What’s more, if they’re good enough, they can even brute-force data packets to HTTPS sites, and steal sensitive data from them too.
And that’s not all - with packet sniffing, hackers can target you with MITM attacks that redirect you to phishing sites. After all, if they know you’re supposed to end up on paypal.com, they could redirect your connection to paupaI.net.org.
If the fake site is good enough, you might be tricked into typing your login credentials (which the hackers will steal and use to empty your account).
How to Protect Yourself from WiFi Packet Sniffing
The solution is pretty simple - just use a VPN. It’s an online tool that hides your IP address and encrypts your traffic. Both perks protect your privacy, but the “encrypts your traffic” part is the one you should be interested in right now.
Here’s what happens:
- You use a VPN app to connect to a VPN server.
- The two establish an encrypted connection between them (called a “tunnel”).
- Any data passing through that connection is encrypted end-to-end, so only the app and server can decrypt it.
- Because of that, nobody can spy on your traffic anymore. If anyone does that, they’ll just see gibberish.
For instance, if a cybercriminal would use a tool like Wireshark to monitor your DNS queries, they won’t see that your requests are heading to “www.paypal.com”. Instead, they’d just see a random string of characters and numbers, like so: “mPF28gomOrmPTpYBGA5zuA==.”
And that’s the kind of thing they’d see when they’d try to monitor any one of your data packets. So they won’t be able to steal sensitive data from you or target you with MITM attacks.
Looking for a reliable VPN service?
Here at SmartyDNS we offer high-speed VPN servers with military grade 256-bit AES encryption and highly secure VPN protocols (OpenVPN, SoftEther and IKEv2), and we we adhere to a strict no-log policy.
Our VPN servers act as proxy servers and we also offer Smart DNS service that allows you to unblock 300+ geo-restricted websites around the world.
We offer convenient VPN apps for Windows, Mac, iPhone / iPad, Android and Fire TV / Stick, and extensions for Chrome and Firefox browsers.
Special offer! Get SmartyDNS for $ 3.7 per month!
Yes, and we’ll also get your 30-day money-back guarantee.
Pro Tip - Use Antivirus Protection Too
Antivirus programs won’t exactly stop packet sniffing, but they can protect you from other related threats.
For instance, let’s say a hacker somehow manages to accurately redirect you to a malicious site even if you’re using a VPN. It takes a lot of luck, sure, but here’s the issue - VPNs can’t protect you from malware. The best they can do is block your connections to malicious domains. But they can’t accurately do that 100% of the time.
In that scenario, antivirus protection is your only line of defense. These programs are designed to quickly prevent and get rid of malware infections.
So make sure you install an antivirus program on all your devices. If you’re not sure which provider to use, try Malwarebytes or ESET.
How Do You Protect Yourself from Packet Sniffing?
Do you just use a VPN, or are there other tools and tips you rely on to protect your data packets? Please tell us about them in the comments below.



